What do we mean by a cyber attack?
A cyber attack is a malicious and an intentional move by an individual or a firm to infringe the information system of another individual or firm. Simply put, a cyber attack maliciously disables a computer, steals data, and impacts resources of others. People involved in cyber attacks use various methods to launch cyber attacks. These methods include malware, ransomware, and phishing, among others.

How does a cyber attack happen?
A cyber attack happens when a cybercriminal tries to get illegal access to the data stored on a different system or on a network while sitting at a distant location. Many cyber attacks are opportunistic, and the hackers involved in the process look for weakness in a computer system and accordingly exploits them. It includes looking for flaws in the code of the website and then inserting the code prepared by the hackers and bypass security and authentication process. There are various means through which the hackers attack the system and damage them via a weak third-party site.
Cyber attacks generally happen via everyday errors like user choosing passwords which can easily be guessed and not changing the default password on the router.
Common forms of cyber attacks
- Denial-of-service (DoS) and distributed denial-of-service (DDoS) attacks:
In this type of cyber attack, a large amount of traffic is sent to various host machines infected by malicious software that is under the control of the attacker. It is a brute force way to prevent some online service to work properly.
Some common examples of these attacks are UDP flooding, SYN flooding & DNS amplification.
- Man-in-the-middle (MitM) attack:
This type of attack happens when the hacker inserts itself between communications that take place between the client and the server. Once the hacker inserts itself between the client and the server, it gains control of the client, and the client’s IP address gets disconnected from the server. The hacker actually replaces the client’s IP address with its own IP address and then spoofs the client’s sequence number. Following this process, the attacker’s computer gives the server a belief that it is communicating with the client.
- Phishing and spear phishing attacks:
In Phishing attacks, the attacker sends an email which appears to come from the trusted sources. The attacker sends these emails with an intention to gain personal details of the user of the system or to influence the user to perform some activity.
Spear phishing is a targeted form of phishing activity where the attacker takes time to do research and then target and create messages that are personal and relevant. The simplest way by which attacker conduct spear phishing is email spoofing.
- Drive-by attack:
A drive-by attack is a common way to spread malware. In this process, the attacker explores insecure websites and then plant a malicious script into HTTP or PHP code on one of the pages which install the malware directly into the system.
- Password attack:
Password attack is the most common way to validate users to an information system to get the password. The password can be obtained by peeping around the person’s desk or system or through social engineering.
- SQL injection attack:
In SQL injection attack process, the attacker exploits the vulnerability to control the database of the victim. These databases are designed using SQL or structured query language. In SQL injection attack, the hacker writes codes in SQL language into the web requesting personal information like name and address. In case the website and the database are not programmed well, then the database could execute those commands.
- Cross-site scripting (XSS) attack:
XSS attacks utilise 3rd-party web resources to execute scripts in the target's web browser or a scriptable application. In this process, the attacker injects a payload with malicious javaScript into a website database. When the victim asks for a page from the website and the website provides a page which has the payload attached as a part of the HTML body to the victim’s browser and executes the malicious script.
- Ransomware:
Ransomware is a form of malware that encrypts the file of the victim, and then the attacker demands a ransom from the victim to restore the data after the payment is processed. The class of this malware is for criminal moneymaking that can be installed via an email, instant message or through the website.
- Malware attack:
These attacks are carried out using malicious software which is installed in the victim’s system without their consent. These softwares can link themselves to any legitimate code and propagate. They can be hidden in useful applications and can replicate itself throughout the internet.
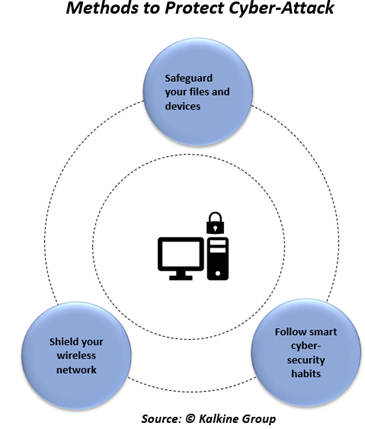
How to protect yourself from a cyber attack?
- Safeguard your files and devices
- Shield your wireless network
- Follow smart cybersecurity habits
What steps to take in case of cyber attack?
- Confirm the breach and discover if any information is compromised.
- Explore what data was stolen or affected.
- Accept the breached organisation’s offer to help.
- Frequently change and use strong login credentials.
- In case of any breach, it is always a good practice to reach out to the breached organisation who could help to recover data.
- Always remain alert and keep a check on accounts.
INTERESTING READ:
 Please wait processing your request...
Please wait processing your request...